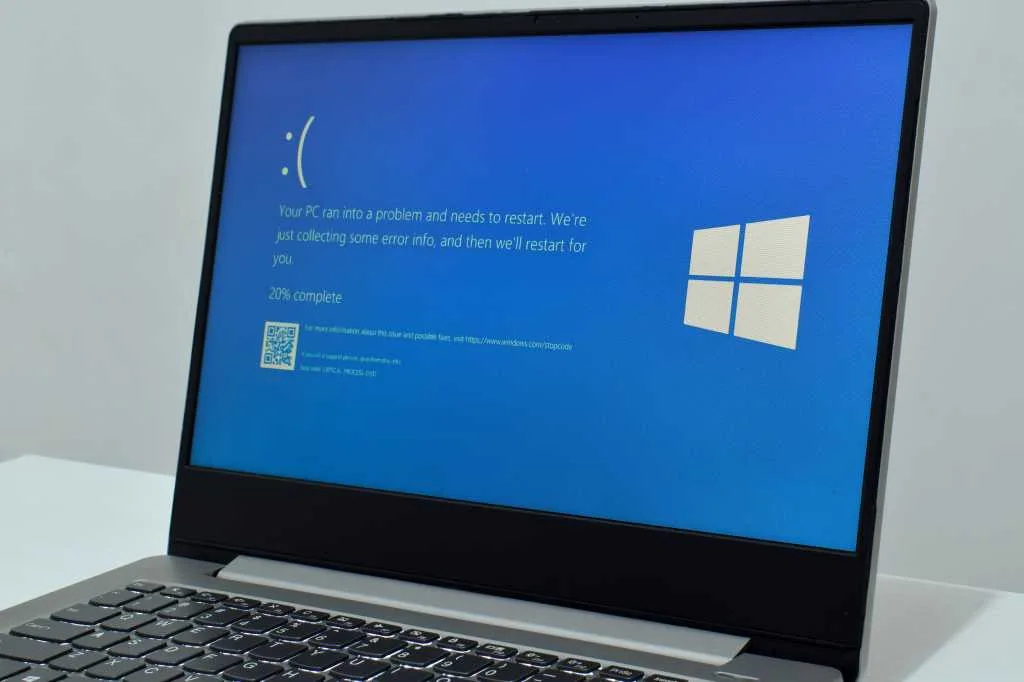
Windows 11 24H2’s March update is riddled with failures and crashes
Just a few days ago, Microsoft released update KB5053598 for Windows 11 24H2, which includes several important security fixes. It’s a mandatory update that’s part of this month’s Patch Tuesday,…